These days, APIs are a necessary tool for tying disparate systems together. They do, however, require a certain amount of intricacy and comprehension to use. At the conclusion, we will include a detailed tutorial on how to do an API security test for those who have read what we have to say on the subject.
Explore the “what,” “why,” and “how” of application programming interface security testing with us. After reading this essay, you should be well-equipped to defend your digital assets in this day of digital disruption.
What Is API Security Testing?
When comparing companies who have implemented APIs to those that have not, the market capitalization of the former has increased by almost 12%. An essential part of making sure APIs are reliable and secure is API Security Testing. Application Programming Interfaces facilitate smooth data interchange by serving as a link between various software systems.
Organizations can foresightedly distinguish and figure out security flaws in their APIs, by undertaking extensive testing. It assesses rate limitation, error handling procedures, input validation strategies, authentication and authorization processes, and other crucial elements. API Security Testing Automation assists companies in strengthening their APIs and protecting sensitive information and resources by utilizing cutting-edge tools, techniques, and industry best practices.
What Is The Importance Of Securing APIs?
As APIs gain popularity, prioritizing their security is increasingly important. Let us explore the significance of API security and the potential ramifications of neglecting it.
One of the most important initial steps in safeguarding sensitive data is to secure APIs. The administration of sensitive data, such as financial information, personally identifiable information (PII), and user passwords, commonly makes use of APIs. Not to add that regulatory compliance requires API security.
Organizations may guarantee compliance with pertinent rules, protect their reputation, and stay out of legal hot water by putting in place security solutions that follow industry standards and best practices.
10 API Vulnerabilities You Must Navigate From
Application programming interfaces (APIs) are crucial for protecting sensitive data and information. Plus, it is vital to maintain the integrity of digital systems. These are ten major API weaknesses that you need to be aware of:
Object Level Authorization Error
Object-level authorization problems happen when an API allows unauthorized users to access certain resources or objects within the system. This vulnerability may allow data to be exposed without the necessary authority, jeopardizing critical data privacy.
Insufficient Authentication
Unauthorized access to APIs may be made possible by inadequate authentication measures. Attackers might be able to take advantage of weak user credential validation or loose authentication policies to pretend to be authorized users and get unauthorized access to the system.
Broken Authorization for Object Property Level
Broken permission for object property level vulnerabilities happen when APIs neglect to include appropriate access controls at the property level, just like object-level authorization problems. This vulnerability could be used by attackers to change object properties and obtain unapproved access.
Unrestricted Resource Consumption
When rate limitation or throttling methods are inadequate, APIs become vulnerable to unrestrained resource use. Attackers can use these vulnerabilities to flood the system with requests. This can resultantly cause denial-of-service (DoS) assaults and system failures.
Broken Function Level Authorization
When APIs neglect to include appropriate authorization checks at the function level, they might lead to broken function level authorization vulnerabilities. This vulnerability could be used by attackers to get around access restrictions and carry out illegal tasks.
Unrestricted Access to Sensitive Business Flows
An important security risk is presented by APIs that allow uncontrolled access to confidential business operations or flows. Attackers might leverage this vulnerability to change important business logic, conduct fraudulent transactions, or obtain personal data.
Server-Side Fraudulent Requests
When APIs give hackers the ability to modify server-side requests in order to obtain access to internal or external systems, server-side request forgery vulnerabilities occur. Data leakage, unauthorized data retrieval, or remote code execution could result from this.
Security Misconfiguration
APIs may be susceptible to exploitation owing to security misconfigurations. These misconfigurations include default settings or improperly configured access controls.Such configuration errors provide an opening for attackers to increase privileges, obtain unauthorized access, or jeopardize system integrity.
Improper Inventory Management
When APIs do not sufficiently manage and safeguard API endpoints, methods, or resources, improper inventory management vulnerabilities arise. Attackers could use this flaw to find and target vulnerable endpoints, raising the possibility of illegal access or data loss.
Unsafe Consumption of APIs
Vulnerabilities arising from improper use or integration techniques of APIs are referred to as unsafe consumption of APIs. This could lead to APIs being vulnerable to many types of attacks, such as injection attacks or data breaches, by disclosing API keys or passwords, transmitting data insecurely, or not performing adequate input validation.

API Security Test and Its Top-Most Types in Use
To guarantee the integrity and security of the interfaces in your applications, API security testing is crucial. To evaluate and improve API security, a variety of techniques are used, each focusing on a distinct facet of risk and vulnerability reduction. Let’s examine the most popular kinds of API security testing now in use:
Dynamic API Security Tests
Black-box testing or dynamic API security tests assess an API’s behavior in real-time by generating requests, checking the answers, and API security testing examples. In order to find vulnerabilities like injection attacks, authentication problems, and data exposure issues, these tests imitate real-world circumstances.
Static API Security Tests
White-box testing, also known as static API security testing, looks at the source code and settings of APIs without running them. These tests find potential vulnerabilities such insecure coding techniques, access control concerns, and exposed sensitive data by examining code and configuration files.
API Fuzzing
In order to find vulnerabilities and unexpected behavior, API fuzzing entails delivering erroneous, unexpected, or corrupt data to APIs. API fuzzing finds possible flaws including buffer overflows, input validation mistakes, and boundary conditions by methodically testing inputs.
API Performance Testing
Application Programming Interface(API) performance testing assesses an API’s scalability, responsiveness, and dependability under varied load scenarios. These assessments monitor response times, throughput, and resource consumption to ensure that APIs can handle expected traffic volumes and offer the greatest experience to end users.
Runtime Application Self-Protection
Real-time application and API call tracking identifies and neutralize security risks, defending APIs and applications from attacks. RASP systems recognize and react to suspicious actions, like unauthorized access attempts or unusual behavior, by monitoring runtime data.
Testing for API Vulnerabilities: Techniques to Verify API Security
APIs enable smooth data flow and communication between disparate systems. Let us know the methods to validate shipping API integration services:
Automated Scanning
The use of automated scanning technologies is essential for carrying out thorough vulnerability analyses of APIs. These best API testing tools analyze request parameters, data payloads, and API endpoints to detect typical security flaws such as injection attacks, broken authentication, and exposed sensitive data.
Fuzz Testing
Sending erroneous, unexpected, or random data inputs to API endpoints is a technique called fuzzing, or fuzzz testing, which is used to find unknown vulnerabilities. Fuzz testing looks for any flaws in input validation, error handling, and boundary conditions by exposing APIs to erratic input variations. By identifying and fixing vulnerabilities before bad actors can take advantage of them, proactive testing lowers the likelihood of security lapses and data breaches for companies.
Manual Testing
Hire QA testers who use focused exploitation techniques and simulated attack scenarios to evaluate an API’s resistance to external threats. With this practical technique, security controls can be thoroughly analyzed and validated, allowing enterprises to efficiently resolve weaknesses and fortify their defenses.
Security Code Review
Examining API source code for potential security flaws and coding mistakes that an attacker could exploit is known as security code review. Security reviewers can offer practical suggestions to enhance code quality and successfully reduce risks by scanning the codebase for typical security mistakes including injection issues, unsecured deserialization, and incorrect access control. In order to reduce the possibility of security events in production systems, proactive security testing helps organizations find and fix vulnerabilities early in the development lifecycle.
Steps To Conduct API Security Testing
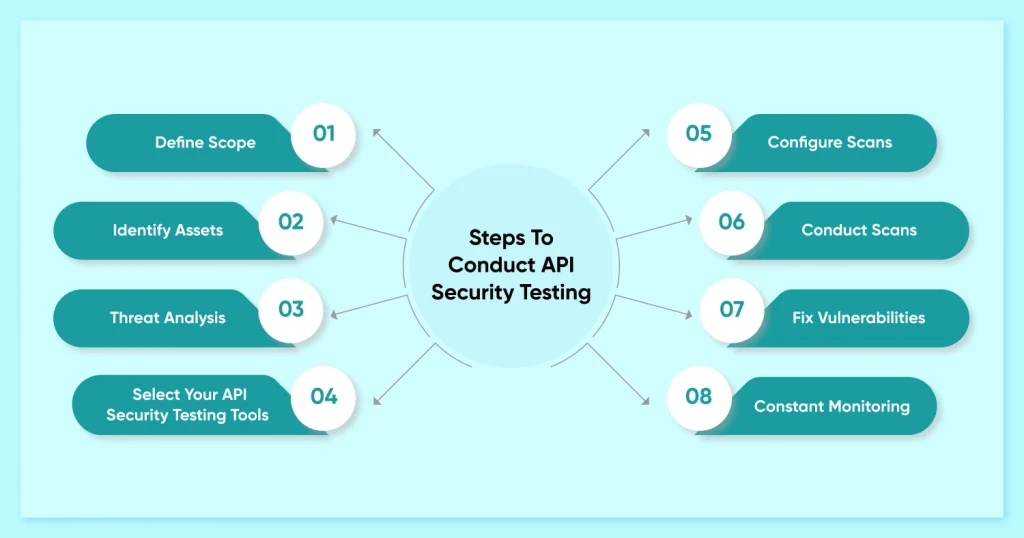
API security scanning allows you to methodically find gaps and weaknesses in your API design.. This enables you to take preventative action to reduce potential risks.To learn how to successfully secure your APIs, let’s dive into the step-by-step process of API security scanning.
Define Scope
Establishing the parameters of your evaluation is the first stage in the API security scanning process. Determine which linked components, APIs, and endpoints you wish to check for security flaws. This entails taking into account APIs that communicate with your systems both inside and externally.
Identify Assets
Following the definition of the scope, list the resources and assets that make up your API ecosystem. This covers third-party connectors, servers, network infrastructure, data repositories, and authentication techniques. A comprehensive security audit requires an understanding of how these resources are interdependent.
Threat Analysis
Identify possible attackers and threats that might endanger your application programming interfaces by doing a threat modeling exercise. Consider factors including improper authentication, data disclosure, injection assaults, denial-of-service (DoS) attacks, and unauthorized access. Security testing can be ranked according to risk by concentrating on the most vulnerable regions.
Select Your API Security Testing Tools
Choose the right technology and techniques for API security scanning according to your needs and financial constraints. A multitude of open-source and commercial technologies are available for code analysis, testing for penetration, and automated vulnerability screening. In your API environment, be sure the functional testing tools you choose work with the formats and protocols that are in use.
Configure Scans
Set up the best API security testing tools in accordance with the goals and scope you have specified. Tailor scan parameters, settings, and authentication techniques to mimic actual attack scenarios. Plan frequent scans to find new vulnerabilities and evaluate how well security controls are working over time.
Conduct Scans
To guarantee correct execution, start the security scans and keep an eye on their progress. Examine the scan results to find any flaws, vulnerabilities, or incorrect setups that were found during the scanning process. Sort the results according to the degree of severity and rank the remedial efforts in that order.
Fix Vulnerabilities
Respond quickly to fix vulnerabilities that have been found and handle security concerns. Use updates, fixes, or configuration changes to strengthen the security posture of your APIs and minimize vulnerabilities. Security policies, procedures, and controls need to be evaluated and updated frequently in order to be robust against evolving threats.
Constant Monitoring
The procedure of API security scanning necessitates constant observation and evaluation. Review and update security scans on a regular basis, adjust to changes in your API environment, and keep up with new threats and vulnerabilities. To limit possible effect and promptly handle security incidents, put in place a strong incident response plan.
Conclusion
In conclusion, in the current digital environment, giving priority to API security testing methodology is critical. Businesses may safeguard their API architecture from assaults by taking a scientific approach, implementing appropriate protocols, and realizing how important it is. Clients and stakeholders are more confident when vulnerabilities are found, risks are decreased, and sensitive data is protected through regular security testing.
Ensuring API security proactively is essential for safeguarding business operations, fulfilling legal requirements, and preserving your brand’s reputation. Organizations may strengthen their defenses against cyberattacks, strengthen their security posture, and confidently traverse the dangerous waters of the contemporary digital world by putting the proper strategies into practice.
Frequently Asked Questions
What Methods Can Be Employed to Evaluate the Security of an API?
Techniques like fuzz testing, penetration testing, and static and dynamic analysis can be used in API security testing. These techniques aid in the identification of weaknesses, evaluate the system’s resistance to erroneous or unexpected input, and model actual attacks in order to evaluate the security of the API.
How to Security Test Rate Limiting on Rest API Security?
Establishing the cutoff point for the quantity of hits or requests. Up until this threshold is reached in terms of requests, all traffic will be allow-listed. Specify how long the threshold will be in effect. Decide whether to use Captcha or a hard block when the volume of requests crosses a certain level.
What Is the Significance of Conducting API Security Testing?
These and other hazards can be reduced with the aid of API security techniques. Robust authorization and authentication procedures contribute to the prevention of data leaks and guarantee that only clients with permission can request APIs. DDoS attacks can be stopped by rate limitation and DDoS defense.
What Strategies Are Recommended for Conducting API Security Testing?
Recognize the needs for APIs.
Indicate the output status of the API.
Prioritize developing tiny, useful APIs.
Arrange the endpoints of the API.
Make use of automation capabilities when testing APIs.
Select an appropriate automation tool.
Select appropriate verification techniques.
Make both affirmative and negative assessments.
What Obstacles Commonly Arise in the Process of API Security Testing?
The Top 6 Difficulties in Testing APIs
Safeguarding REST API Combinations of Parameters.
Verifying the Parameters of REST APIs.
Keeping Data Formatting Up to Date.
Safeguarding API Call Chains.
Configuring a REST API Test Automated.
Reporting errors with REST APIs.







